Chapter III: Your Greatest Asset Isn’t Your People. It’s the Data About Your People
An industry “influencer” recently posted a “SCAM ALERT” (his emphasis, not mine) alerting other recruiters to an enterprise employer whose candidate experience was, apparently, being imperiled by what seems like a scam so simple and straightforward that one has to admire the pure efficiency of the social engineering at play.
The company in question, a major multinational employer, was seeing its job postings scraped from its corporate careers site, reposted on third party sites, and candidates were encouraged to directly apply through this intermediary, which was, in fact, in no way affiliated with the company’s recruiting efforts.
For years, this was basically Indeed’s entire business model, but apparently the morality line for most isn’t the basic theft of intellectual property through aggregation and deduplication – and the effective hijacking of their employment related SEO/SEM from the “world’s #1 job site” has become codified instead of vilified for reasons I don’t quite understand.
The major difference was that Indeed was built to drive these candidates to the employers and jobs they were looking for in the hope of monetizing the multi-billion dollar market for online job advertising – 85 percent of which, according to Mary Meeker’s annual Internet Trends report, comes from Google and Facebook, both of whose recruiting plays probably means Indeed’s claim to the top spot is now not only misleading, but inaccurate as well.
This new “fraud,” as it were, collects those candidates and instead of passing them off to the company in question, poses as recruiters themselves, hoping to obtain information such as addresses, dates of birth, Social Security numbers and all the other information required to commit identity theft (by far the fastest growing crime in the world) – and making money off of the candidate through essentially phishing this information under the guise of representing legitimate employment opportunities.
Why hackers may be doing your company a favor
Most recruiters and HR practitioners will likely howl at this duplicity – and, judging from the comment string, most are shocked, shocked! that anyone would hoodwink a random online applicant by asking for information like their SSN, despite the fact that our applicant tracking systems have done this for years and actually made it seem completely innocuous and commonplace.
Here’s the thing: These hackers are probably doing your company a favor by screening out those candidates who would be susceptible to these schemes before they’re employees, and before they have access to your enterprise systems and you assume liability as an employee.
In fact, I’d actually encourage employers to do this sort of white hat threat analysis as part of their internal mobility and promotions process, as a means of identifying which employees present the biggest risk to what’s quickly becoming the biggest danger to the biggest asset any employer has.
Hint: It’s not people. It’s the data about your people that is what The Economist recently labeled as “The New Oil” for its valuation and commoditization. An anecdote: When Caesar’s Entertainment filed for Chapter 11 bankruptcy, the federal judge assigned to unwind the conglomerate ruled that the company’s most valuable asset was not its prime properties on some of the world’s most expensive real estate – think Macau and the Las Vegas Strip – it was, in fact, the 17 years of Player’s Club data the company had collected before it was dissolved.
If the habits and preferences of gamblers, individually or in aggregate, is worth more than any asset of a friggin’ casino conglomerate, think about how much the data stored by your ATS or HCM is worth – both to your business, and to the proliferation of hackers looking to illicitly obtain it.
We think of data breaches as being from state actors sitting in front of sophisticated terminals somewhere in East Asia or beneath Moscow, or some Mr. Robot-style lone actor systematically targeting individual instances, but in fact, that’s pure Hollywood (or “fake news,” if you will, comrade).
The fact is, the majority of enterprise data breaches are caused by employee negligence and human error, driven not by sophisticated technologies and black hat techniques, but through the most seemingly innocuous of means: email. And as most workers still live their work lives through their inbox, this means your business, likely, is at risk of having its information compromised.
Get ready for more big data breaches
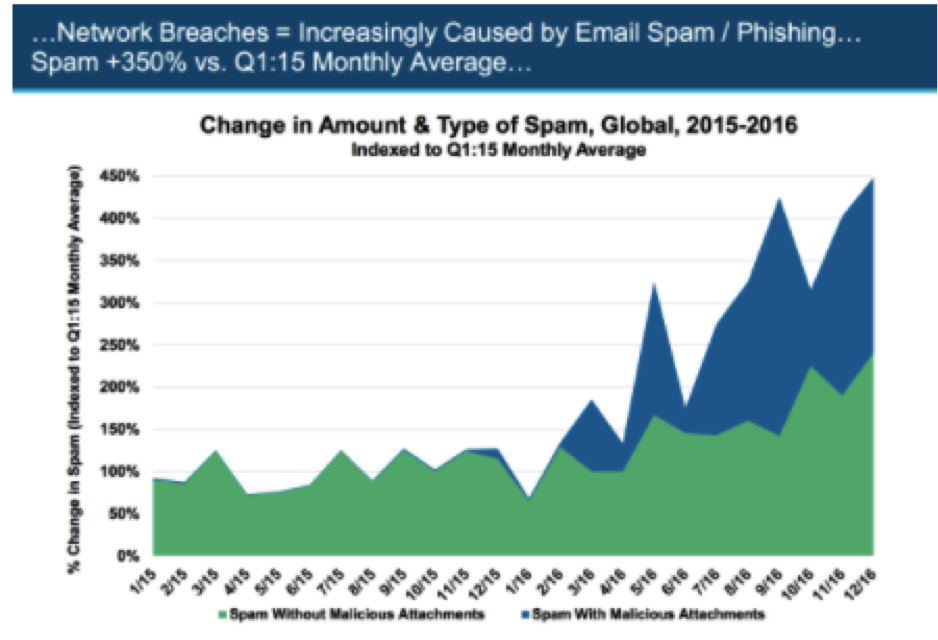
Meeker’s report suggested a significant spike in spam with malicious attachments, malware or links to third party sites which contain the spyware or ransomware necessary to either capture enterprise data or personally identifiable information, or else hold that data hostage until their demands are paid (or the data deleted).
These breaches have become commonplace in headlines, with notable recent attacks shutting down institutions like the UK’s National Health Service or stealing millions from the Central Bank of Bangladesh – seemingly sophisticated and devastating breaches that were not the result of external intrusion, but rather, internal negligence.
In one instance, ransomware overrode centralized servers through what seems like an everyday oversight – enterprise network administrators neglecting to update obsolete (and exploitable) instances of Windows XP.
Of course, if your company is still on this OS, you probably have a host of other concerns, but here’s the rub: The people charged with preventing these incidents failed at the fundamental part of their job.
Those of us who aren’t necessarily charged with monitoring our networks and servers from breaches or malicious attacks are far more susceptible to falling for the trick that enabled the world’s largest ever bank heist, and one that’s already targeting candidates and companies alike – phishing scams, in which end users unknowingly grant malware access to their networks not via the backdoor, but inviting them in through our inboxes.
And these type of attacks are just heating up, with trend data in Meeker’s report suggesting these attacks should surge over the months and years to come. Sending data to unknown external parties, opening external attachments and constantly enabling third party software to collect PII for the purposes of expediency (see: every “free” sourcing tool ever) is a core part of recruiting, and applicant tracking and HCM systems are obviously a gold mine of exactly the type of information that are the most valuable to intruders.
While many spoke to standard security protocols and compliance certifications on their website, I could find no mention on any of the major resume parsing or traditional job board sites on how they were able to guarantee that their attachments were in fact, resumes or profiles as promised, rather than being Trojan horses looking for easy access to the potentially millions of records sitting on your enterprise servers.
Better start training employees and hires on data security — NOW
I’m sure they have talking points, but there’s no way that your major HR Technology vendors can ever innovate quickly enough to totally forestall the rapidly evolving infosec landscape and preempt the proliferation of new schemes and scams and software.
The best that they can hope to do is monitor their servers for suspicious activity and simply shut down their systems before any large scale data breach can occur. This has occurred several times across multiple vendors in the past year alone, and to date, the decision to keep all users out has caused some recruiter consternation, but also preempted any sort of major breach or, in the age of SaaS, total data dump of all clients using a particular ATS or HCM.
This will happen, and the onus is going to be on vendors to increasingly come up with capabilities for preempting this.
But just as importantly, it’s up to recruiters and HR professionals to continually train employees and screen new hires on what’s becoming the most critical competency of the 21st Century – information security. As a side note, I’d highly discourage that whole BYOD thing, but that’s another post entirely.
We talk a lot about culture in recruiting and talent, but this is generally specious shit like office accoutrements, physical workspaces and propaganda videos from brainwashed, beautiful employees talking about how kick ass their company is.
But the companies that win in the future aren’t going to do so because they’ve built a culture of ping pong tables, open seating and flat hierarchies. They’re going to do so because they’ve built their culture around security, and every employee is actively aware of and engaged in preempting and preventing this growing category of cybercrime. A one off course during onboarding or an annual review simply won’t do it.
Prompting password changes every 30 days also won’t do it. But, a shared value and commitment to protecting our companies’ information – and keeping our co-workers and colleagues’ information safe – will at least stanch the bleeding that’s already starting to trickle out of our tech. If data security isn’t part of your company’s mission, vision and values, well, you’re probably in for a rude awakening.
And if you don’t send $500 in Bitcoin to [email protected], well, let’s just say you should have quit reading this a couple thousand words ago. But if you share it on social or leave a comment below, we might unencrypt that POS Lenovo your company gave you anyway.
Did you miss the first two parts of this series? Check out The State of Internet for Recruiting and Hiring, and, The New Internet Echo Chamber.
By Matt Charney
Matt serves as Chief Content Officer and Global Thought Leadership Head for Allegis Global Solutions and is a partner for RecruitingDaily the industry leading online publication for Recruiting and HR Tech. With a unique background that includes HR, blogging and social media, Matt Charney is a key influencer in recruiting and a self-described “kick-butt marketing and communications professional.”
Recruit Smarter
Weekly news and industry insights delivered straight to your inbox.